Setup Arp Centos
Using pf. Blocker. NG And Block Lists On pf. Sense Linux Included. Share this post In a previous post, I talked about implementing blocklists aka IP reputation lists, ban lists, blacklists, etc. The examples I used were on pf. Sense and OPNsense. I also discussed the methodology and some background as well so if youre just coming into the conversation, it might be worth a read beforehand. Free Computer Networking Notes, Guides, Tutorials for CCNA, Comptia N, MCSE, RHCE Certification. Users of Windows Server 2012 will benefit from numerous innovations, especially in the areas of virtualization, high availability, and storage. In. 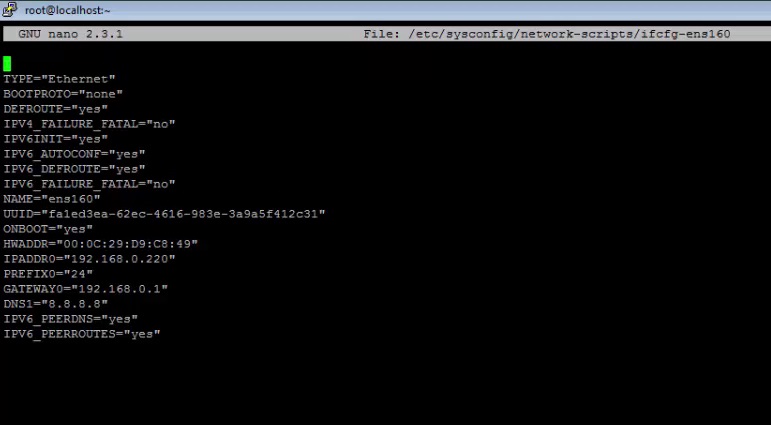 Previous Post Using Firewall Block ListsThere were some downfalls to the previously discussed approach such as the URL download via aliases only allowed updates every 1 day as the shortest timeframe. In addition, the list had to be in a very specific format so I originally wasnt able to use known, high quality lists with split fields like the original formats provided by DShield Internet Storm Center or Emerging Threats. Yes, I realize I could easily script this up to get rid of both of these limitations, but why if you dont need to If you are using pf. Sense, there is a really cool plug in called pf. Blocker. NG that gets around many of these issues. Setup Arp Centos' title='Setup Arp Centos' />
Previous Post Using Firewall Block ListsThere were some downfalls to the previously discussed approach such as the URL download via aliases only allowed updates every 1 day as the shortest timeframe. In addition, the list had to be in a very specific format so I originally wasnt able to use known, high quality lists with split fields like the original formats provided by DShield Internet Storm Center or Emerging Threats. Yes, I realize I could easily script this up to get rid of both of these limitations, but why if you dont need to If you are using pf. Sense, there is a really cool plug in called pf. Blocker. NG that gets around many of these issues. Setup Arp Centos' title='Setup Arp Centos' /> Article on how to install ease to use, webinterface based, open source TV streaming server TvHeadend in Linux Mint 17. Duratec conversion parts list confirmation Just a quick check of parts required to convert Pinto to Duratec and likely source Engine Mounts Fisher Fury as it is. Blocker. NG is a free package originally written by some other folks, but now maintained by BBcan. Twitter. Ive been pretty harsh on pf. Blocker over the years because it was primarily a way to blacklist countries based on IP ranges I didnt agree with this approach because it doesnt work for most businesses and it would inevitably block much needed customer traffic at some point and it was a PITA to troubleshoot. While that particular functionality still exists in the package, I wont talk about it here. Keep in mind this feature may be useful depending on your use case. Linux Networking Paul Cobbaut Paul Cobbaut Publication date 20150524 CEST Abstract This book is meant to be used in an instructorled training. For selfstudy, the. Learn how to set up your Raspberry Pi without a monitor or keyboard and how to configure it to operate as a remote desktop. This article shows steps to enable Outlook Anywhere in Exchange 2010. In order to access emails via Outlook application, Outlook Anywhere. Setup Arp Centos' title='Setup Arp Centos' />Instead, Ill talk about using IPv. Blocker. NG. At this point, Im assuming you have already installed the package. If not, go do so and Ill wait hereAfter installing the package, you will need to enable it from the main page. Change the settings on the main screen as necessary. Items worth noting include that I would check the interfaces to verify all of your networks are there and the kill states is checked. Next, go to the IPv. I already discussed the ban list from Binary Defense in the last blog. The IP banlist updates every 5 minutes and while we wont update every 5 minutes, we are going to set it up to update every hour as shown below. The other difference is that we will set the list action to deny both to create firewall rules blocking traffic in both directions to offending IP addresses. Note the headerlabel BDIPs for this example is simply used as a placeholder. The label should, however, have something signifying which list it originates from. Ill explain this a bit more later. Great So we did the same thing as the previous post did with aliases, but now we are updating once an hour instead of once a day. What else can we doThe big change is that we can add other lists in various formats. In addition to a huge, clean list of IP addresses like the banlist. Binary Defense, we can also add list formats such as those used by Emerging Threats and DShield. Both of these include CIDRs 1. IP addresses vs. single IP addresses. For what it is worth, you may have also seen previously that you can tie multiple blacklists to a single alias. So you may be asking, why am I separating them here Based on experience, the free Emerging Threats lists only only update every few days so to avoid unnecessary calls to their servers, once a day should suffice. The one block list from Emerging Threats already includes the aforementioned CIDRs from DShield so we dont need to include that list separately as shown below. Block IPs. txt. Information from that feed headerThose DShield CIDRs are also listed at the bottom of that feed Emerging Threats fwip rules. Raw IPs for the firewall block lists. These come from Spam nets identified by Spamhaus www. Top Attackers listed by DShield www. Abuse. ch More information available at www. The URL for the other list is below. After we add both URLs, the identifying headerslabels, change list action to deny both, and update frequency to once a day we are ready to go. Click save and if you followed my naming conventions, your aliases under IPv. Update firehollevel. March 2. 01. 7I was notified of the numerous ban lists on http iplists. Overall, the site has great explanations on the ins and outs of the various lists. Their comparisonsmetrics include what percent of one list is included in another list, which ones might yield false positives, how an IP address would get added to a list, etc. After testing in a few environments for several weeks, I found the firehollevel. I havent yet experienced a false positive. You configure firehollevel. Binary Defense list was configured above, i. I also chose to update from the Git. Hub feed vs. the firehol. Note There are other feeds there that might be useful on the site as well. I chose the firehollevel. Firewall Rules. If you go to the firewall rules section of your firewall, you should see two or three separate rules added automatically on the WAN side. Similar rules should have been added to the LAN side as well Remember we are blocking in both directions. WANLANAs previously described, you can once again hover over either of the rules to see if the IP addressesranges have been pulled back by the firewall cron entry we setup a short time ago. You can also go to the diagnostics, table, pf. Byour list name to look at all of the IP addresses and ranges for that particular aliaslist. The update page for pf. Blocker. NG also tends to be pretty solid if you need some assistance troubleshooting, e. You can also force updates, see when the next run time is, etc. Last, but not least Is it working The alerts page on pf. Blocker. NG shows you timestamps for blocked IPs, what interface it was on, what rule triggered the block or reject, etc. Note in the example above Im seeing blocks on the WAN side. If youre seeing blocks on the LAN, that means an internal machine is attempting to contact a known malicious IP address and is really, really ridiculously bad In all seriousness, keep an eye out for blocks on the LAN side as that can be a fantastic indicator that one of your internal machines is compromised. The Sims 3 Final Fantasy Mods.
Article on how to install ease to use, webinterface based, open source TV streaming server TvHeadend in Linux Mint 17. Duratec conversion parts list confirmation Just a quick check of parts required to convert Pinto to Duratec and likely source Engine Mounts Fisher Fury as it is. Blocker. NG is a free package originally written by some other folks, but now maintained by BBcan. Twitter. Ive been pretty harsh on pf. Blocker over the years because it was primarily a way to blacklist countries based on IP ranges I didnt agree with this approach because it doesnt work for most businesses and it would inevitably block much needed customer traffic at some point and it was a PITA to troubleshoot. While that particular functionality still exists in the package, I wont talk about it here. Keep in mind this feature may be useful depending on your use case. Linux Networking Paul Cobbaut Paul Cobbaut Publication date 20150524 CEST Abstract This book is meant to be used in an instructorled training. For selfstudy, the. Learn how to set up your Raspberry Pi without a monitor or keyboard and how to configure it to operate as a remote desktop. This article shows steps to enable Outlook Anywhere in Exchange 2010. In order to access emails via Outlook application, Outlook Anywhere. Setup Arp Centos' title='Setup Arp Centos' />Instead, Ill talk about using IPv. Blocker. NG. At this point, Im assuming you have already installed the package. If not, go do so and Ill wait hereAfter installing the package, you will need to enable it from the main page. Change the settings on the main screen as necessary. Items worth noting include that I would check the interfaces to verify all of your networks are there and the kill states is checked. Next, go to the IPv. I already discussed the ban list from Binary Defense in the last blog. The IP banlist updates every 5 minutes and while we wont update every 5 minutes, we are going to set it up to update every hour as shown below. The other difference is that we will set the list action to deny both to create firewall rules blocking traffic in both directions to offending IP addresses. Note the headerlabel BDIPs for this example is simply used as a placeholder. The label should, however, have something signifying which list it originates from. Ill explain this a bit more later. Great So we did the same thing as the previous post did with aliases, but now we are updating once an hour instead of once a day. What else can we doThe big change is that we can add other lists in various formats. In addition to a huge, clean list of IP addresses like the banlist. Binary Defense, we can also add list formats such as those used by Emerging Threats and DShield. Both of these include CIDRs 1. IP addresses vs. single IP addresses. For what it is worth, you may have also seen previously that you can tie multiple blacklists to a single alias. So you may be asking, why am I separating them here Based on experience, the free Emerging Threats lists only only update every few days so to avoid unnecessary calls to their servers, once a day should suffice. The one block list from Emerging Threats already includes the aforementioned CIDRs from DShield so we dont need to include that list separately as shown below. Block IPs. txt. Information from that feed headerThose DShield CIDRs are also listed at the bottom of that feed Emerging Threats fwip rules. Raw IPs for the firewall block lists. These come from Spam nets identified by Spamhaus www. Top Attackers listed by DShield www. Abuse. ch More information available at www. The URL for the other list is below. After we add both URLs, the identifying headerslabels, change list action to deny both, and update frequency to once a day we are ready to go. Click save and if you followed my naming conventions, your aliases under IPv. Update firehollevel. March 2. 01. 7I was notified of the numerous ban lists on http iplists. Overall, the site has great explanations on the ins and outs of the various lists. Their comparisonsmetrics include what percent of one list is included in another list, which ones might yield false positives, how an IP address would get added to a list, etc. After testing in a few environments for several weeks, I found the firehollevel. I havent yet experienced a false positive. You configure firehollevel. Binary Defense list was configured above, i. I also chose to update from the Git. Hub feed vs. the firehol. Note There are other feeds there that might be useful on the site as well. I chose the firehollevel. Firewall Rules. If you go to the firewall rules section of your firewall, you should see two or three separate rules added automatically on the WAN side. Similar rules should have been added to the LAN side as well Remember we are blocking in both directions. WANLANAs previously described, you can once again hover over either of the rules to see if the IP addressesranges have been pulled back by the firewall cron entry we setup a short time ago. You can also go to the diagnostics, table, pf. Byour list name to look at all of the IP addresses and ranges for that particular aliaslist. The update page for pf. Blocker. NG also tends to be pretty solid if you need some assistance troubleshooting, e. You can also force updates, see when the next run time is, etc. Last, but not least Is it working The alerts page on pf. Blocker. NG shows you timestamps for blocked IPs, what interface it was on, what rule triggered the block or reject, etc. Note in the example above Im seeing blocks on the WAN side. If youre seeing blocks on the LAN, that means an internal machine is attempting to contact a known malicious IP address and is really, really ridiculously bad In all seriousness, keep an eye out for blocks on the LAN side as that can be a fantastic indicator that one of your internal machines is compromised. The Sims 3 Final Fantasy Mods.